Understanding Network
Trace-route
This week we learn about traceroute by tracing website’s real location by finding its IP address then tracing its physical location of the that webpage
using terminal command : $ traceroute IPADDRESS
This command will test the connection between two points; such as my router to a website on the internet, by sending a small package ( max = 64 hops ) across the network; which we can get the IP Address of our destination by this command : $ nslookup www.example.com
Using Traceroute mapper to trace the IP addresses of some of my most visited site, I found that it’s very interesting that not only my most US visited pages are all served from here in the US but my most visited Thai pages that I thought the server should be somewhere in asia or europe are also served in the US as well - which I think they might just separated their server for the users in each continent.
Most of the route is traveling across the country from location in NYC to LA or San Fransisco and most of the time the request was blocked and went to the maximum hops.
One of my most visited Thai news site ; www.prachatai.com, got all its connection only in the US.
Facebook’s connections are also traveling crossed the Philadelphia and SF like some of my other most visited sites.
Firewall log
After setting up droplet server on Digital Ocean, installing an uncomplicated firewall (ufw) and waited for a couple days, I followed the Understanding Networks guide and found that I had forgotten my password ( -”- ) and have to re-do my droplet all over again.
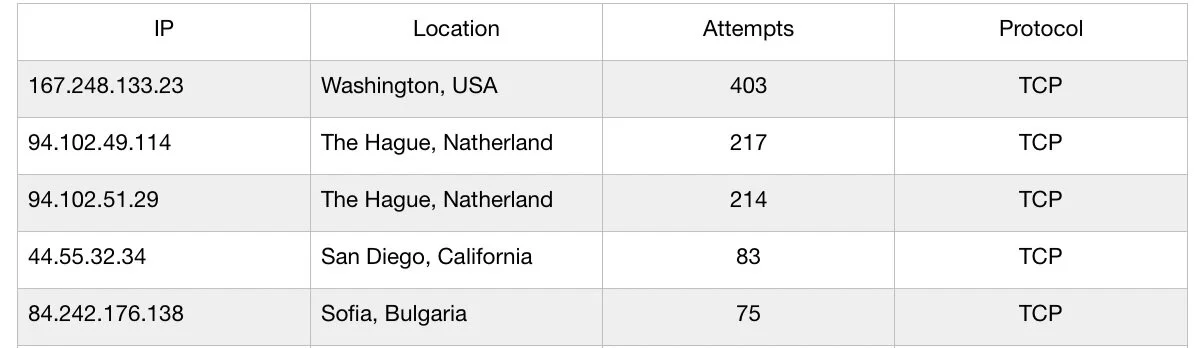
I waited for another couple days apparently there are 11965 pings to my firewall. Then,I followed Tom's firewall video to create a google sheet of the pings and checked the IP address with ipinfo.io .
After checking the list of the IP address that attempted to get to my firewall host I found it’s very interesting to see how much information we could get from the IP address number which is only a gibberish to me before this class.
My most connections are from Washington DC and the Hague, Netherland which they were trying to poke to the host aggressively with TCP protocol. Interestingly there is also some IP that try to attack my host for only a few times - What would that mean?
Here is the list of top IP addresses that try to connect to my host :